- Harvard PhD removes the last "hard bone" in soft robots and a flexible computer is born
-
 Introduction: In recent years, soft robots have developed rapidly. They can't wait to remove the "hard bones" in their bodies - metal parts. On this road to removal, Preston, a postdoctoral fellow from Harvard, made...
Introduction: In recent years, soft robots have developed rapidly. They can't wait to remove the "hard bones" in their bodies - metal parts. On this road to removal, Preston, a postdoctoral fellow from Harvard, made...
-
Keywords:
soft robot
robot
computer
Publish Time:2019-04-01
- Design of wireless sensor nodes for the Internet of Things
-
 Wireless sensor nodes (WSN) play a key role in promoting the development of the Internet of Things (IoT). The advantages of WSN are that it has extremely low power consumption, extremely small size, and easy installation....
Wireless sensor nodes (WSN) play a key role in promoting the development of the Internet of Things (IoT). The advantages of WSN are that it has extremely low power consumption, extremely small size, and easy installation....
-
Keywords:
Internet of Things
Wireless Sensors
Nodes
Publish Time:2018-03-13
- How does an orange peel unlock fingerprint recognition? The key lies in the conductive pen coating
-
 Recently, the issue of Orange Peel unlocking fingerprint recognition has been all over major social forums and media. Many mobile phones have not escaped this bug. Many people said that they felt terrible after watching the video and called on "God" to explain it....
Recently, the issue of Orange Peel unlocking fingerprint recognition has been all over major social forums and media. Many mobile phones have not escaped this bug. Many people said that they felt terrible after watching the video and called on "God" to explain it....
-
Keywords:
Orange peel
unlock
fingerprint recognition
Publish Time:2018-01-29
- Near-infrared imaging technology promotes new developments in machine vision
-
 Machine vision is traditionally defined as electronic imaging for inspection, process control, and automated navigation. In machine vision applications, computers (not humans) use imaging technology to capture images as input....
Machine vision is traditionally defined as electronic imaging for inspection, process control, and automated navigation. In machine vision applications, computers (not humans) use imaging technology to capture images as input....
-
Keywords:
Near infrared imaging
machine vision
Publish Time:2017-11-28
- MIT announces top 10 scientific achievements of 2017: facial recognition payment, thermal energy batteries, etc. are on the list
-
 According to foreign media reports, MIT announced the top ten scientific and technological achievements of the year, including helping paralyzed patients walk again, "face recognition" becoming a means of payment, and the gradual rise of artificial intelligence... These scientific and technological achievements...
According to foreign media reports, MIT announced the top ten scientific and technological achievements of the year, including helping paralyzed patients walk again, "face recognition" becoming a means of payment, and the gradual rise of artificial intelligence... These scientific and technological achievements...
-
Keywords:
Heat
cells
paralysis
MIT scientists
Publish Time:2017-02-24
- Black technology is not just VR. Check out the technologies you don’t know about.
-
 In the past, various future black technologies have appeared in front of us in a very high-end form, especially in science fiction novels or movies. However, the black technologies related to display have always been more...
In the past, various future black technologies have appeared in front of us in a very high-end form, especially in science fiction novels or movies. However, the black technologies related to display have always been more...
-
Keywords:
Black technology
VR
Publish Time:2016-09-28
- In-depth | Hacker Only_Guest tells: How to kill a scammer gracefully?
-
 He is the leader of the PKAV team that vows to compete with AV for otakus; he is a hacker who must drink two sips of hacker beer before every speech; he once hacked the food city recharge card and enjoyed a free meal; he once located the entire...
He is the leader of the PKAV team that vows to compete with AV for otakus; he is a hacker who must drink two sips of hacker beer before every speech; he once hacked the food city recharge card and enjoyed a free meal; he once located the entire...
-
Keywords:
Hacker
Only_Guest
Anti-telecom fraud
Publish Time:2016-09-26
- Five issues to consider when designing a data center
-
 Here are five key questions to ask yourself to ensure your data center design stays on the right track: 1. How many racks do you need? What size are they? The number of racks determines the space in your data center....
Here are five key questions to ask yourself to ensure your data center design stays on the right track: 1. How many racks do you need? What size are they? The number of racks determines the space in your data center....
-
Keywords:
Data center
integrated wiring
data center market
Publish Time:2016-07-13
- Verint helps RedOwl management and monitoring platform add voice capabilities
-
Verint® Systems Inc. has announced a global partnership with RedOwl, a leader in human risk analysis. The two companies will integrate their technologies...
-
Keywords:
Verint
RedOwl
management and monitoring platform
voice function
Publish Time:2016-06-01
- A brief discussion on cloud storage technology architecture
-
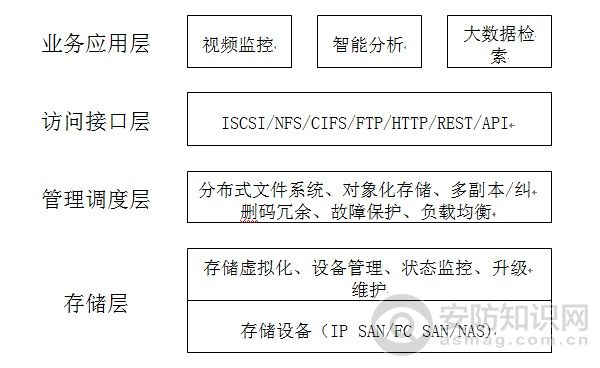 At present, the construction mode of using technology to assist urban management has shifted from the previous safe city construction based on video surveillance to the smart city construction based on multi-sensor technology. In this process,...
At present, the construction mode of using technology to assist urban management has shifted from the previous safe city construction based on video surveillance to the smart city construction based on multi-sensor technology. In this process,...
-
Keywords:
Cloud storage technology architecture
Publish Time:2016-05-16
- How to prevent hackers from invading your home network?
-
 Smartphones, tablets, laptops, personal PCs, smart lights, smart sockets... More and more devices at home need to connect to WiFi, and these devices are connected through the wireless router in our home....
Smartphones, tablets, laptops, personal PCs, smart lights, smart sockets... More and more devices at home need to connect to WiFi, and these devices are connected through the wireless router in our home....
-
Keywords:
hacker
home network
wireless router
Publish Time:2016-01-26
- It's time to kill the password
-
 Many digital stories show that passwords are becoming a thing of the past and cannot support the trillion-dollar mobile payment market. In 2014, there were 1,500 data leaks worldwide and 1 billion pieces of personal information were stolen....
Many digital stories show that passwords are becoming a thing of the past and cannot support the trillion-dollar mobile payment market. In 2014, there were 1,500 data leaks worldwide and 1 billion pieces of personal information were stolen....
-
Keywords:
Fingerprint recognition
Publish Time:2015-04-30
- A brief analysis of four major issues in the development of SDN technology
-
At today's 2015 China SDN NFV Conference, Liu Duo, Vice President of the China Academy of Information and Communications Technology and Secretary-General of the SDN Industry Alliance, said that the SDN industry development white paper was officially released and the white paper introduced...
-
Keywords:
technology
technological development
development
four
Publish Time:2015-04-24
- Coverage Testing of Embedded Software
-
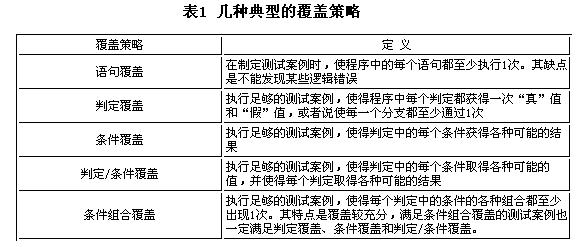 1 Overview Software testing is a very broad concept. From the perspective of its running through the entire software life cycle, testing can be divided into stages such as module testing, integration testing, and system testing. Testing can also be divided into static checking and...
1 Overview Software testing is a very broad concept. From the perspective of its running through the entire software life cycle, testing can be divided into stages such as module testing, integration testing, and system testing. Testing can also be divided into static checking and...
-
Keywords:
Embedded software
coverage testing
Publish Time:2015-03-13
- Customization Features of the MAXQ3120 Energy Meter Reference Design
-
 The MAXQ3120 electricity meter (EM) reference design builds a multifunction, multirate electricity meter that complies with all applicable standards worldwide....
The MAXQ3120 electricity meter (EM) reference design builds a multifunction, multirate electricity meter that complies with all applicable standards worldwide....
-
Keywords:
MAXQ3120
electric meter
custom functions
Publish Time:2015-03-13
- Gesture tracking is the future of interaction, so how to solve tactile feedback
-
 The rise of smartphones allows us to interact with machines by tapping on touch screens. So what other ways of interaction will humans develop behind this small piece of glass? Will we interact with devices through voice? Or will we wear augmented reality glasses and receive the information we need all day? Or will we use touch......
The rise of smartphones allows us to interact with machines by tapping on touch screens. So what other ways of interaction will humans develop behind this small piece of glass? Will we interact with devices through voice? Or will we wear augmented reality glasses and receive the information we need all day? Or will we use touch......
-
Publish Time:2015-01-03
- New security storage technology protects data security from the bottom up
-
In recent years, with the continuous development of information technology and the popularization and application of security products and systems, data security issues in the security industry have been paid more and more attention. With the rapid development of high-definition monitoring, the large-scale deployment of large-scale projects such as safe cities and smart cities, the amount of data is increasing, and the storage of big data is also increasing......
-
Publish Time:2014-12-16
- Analysis of the development prospects of face recognition technology in 2015
-
 The development of face recognition technology in China started in the late 1990s and has gone through five stages: "technology introduction - professional market introduction - technology improvement - technology application - use in various industries and fields". So far, with the continuous maturity of domestic face recognition technology, this technology has been increasingly used......
The development of face recognition technology in China started in the late 1990s and has gone through five stages: "technology introduction - professional market introduction - technology improvement - technology application - use in various industries and fields". So far, with the continuous maturity of domestic face recognition technology, this technology has been increasingly used......
-
Publish Time:2014-11-28
- IoT Applications: A Brief Discussion on Zhixintong OBD Internet of Vehicles Platform
-
In this era of E-sports, cars have become an indispensable part of people's lives. With the rapid development of technology and the continuous improvement of living standards, people's requirements for car maintenance are also rising. In such an era, the Internet of Vehicles, a mysterious role that used to be silent, has become......
-
Publish Time:2014-11-28
- “Follow the map” in the context of big data
-
 Big Data Analysis What is Big Data? Big data is usually used to describe a large amount of unstructured or semi-structured data. It takes a lot of money to convert such data into relational data for future analysis. Big data technology is......
Big Data Analysis What is Big Data? Big data is usually used to describe a large amount of unstructured or semi-structured data. It takes a lot of money to convert such data into relational data for future analysis. Big data technology is......
-
Publish Time:2014-11-20
Open Source Project Recommendations
Latest Security Electronics Articles
MorePopular Resource Recommendations
MorePopular Headline Technical Articles
MorePotentially Interesting Components
MorePopular Download Recommendations
 Introduction: In recent years, soft robots have developed rapidly. They can't wait to remove the "hard bones" in their bodies - metal parts. On this road to removal, Preston, a postdoctoral fellow from Harvard, made...
Introduction: In recent years, soft robots have developed rapidly. They can't wait to remove the "hard bones" in their bodies - metal parts. On this road to removal, Preston, a postdoctoral fellow from Harvard, made...
 Wireless sensor nodes (WSN) play a key role in promoting the development of the Internet of Things (IoT). The advantages of WSN are that it has extremely low power consumption, extremely small size, and easy installation....
Wireless sensor nodes (WSN) play a key role in promoting the development of the Internet of Things (IoT). The advantages of WSN are that it has extremely low power consumption, extremely small size, and easy installation....
 Recently, the issue of Orange Peel unlocking fingerprint recognition has been all over major social forums and media. Many mobile phones have not escaped this bug. Many people said that they felt terrible after watching the video and called on "God" to explain it....
Recently, the issue of Orange Peel unlocking fingerprint recognition has been all over major social forums and media. Many mobile phones have not escaped this bug. Many people said that they felt terrible after watching the video and called on "God" to explain it....
 Machine vision is traditionally defined as electronic imaging for inspection, process control, and automated navigation. In machine vision applications, computers (not humans) use imaging technology to capture images as input....
Machine vision is traditionally defined as electronic imaging for inspection, process control, and automated navigation. In machine vision applications, computers (not humans) use imaging technology to capture images as input....
 According to foreign media reports, MIT announced the top ten scientific and technological achievements of the year, including helping paralyzed patients walk again, "face recognition" becoming a means of payment, and the gradual rise of artificial intelligence... These scientific and technological achievements...
According to foreign media reports, MIT announced the top ten scientific and technological achievements of the year, including helping paralyzed patients walk again, "face recognition" becoming a means of payment, and the gradual rise of artificial intelligence... These scientific and technological achievements...
 In the past, various future black technologies have appeared in front of us in a very high-end form, especially in science fiction novels or movies. However, the black technologies related to display have always been more...
In the past, various future black technologies have appeared in front of us in a very high-end form, especially in science fiction novels or movies. However, the black technologies related to display have always been more...
 He is the leader of the PKAV team that vows to compete with AV for otakus; he is a hacker who must drink two sips of hacker beer before every speech; he once hacked the food city recharge card and enjoyed a free meal; he once located the entire...
He is the leader of the PKAV team that vows to compete with AV for otakus; he is a hacker who must drink two sips of hacker beer before every speech; he once hacked the food city recharge card and enjoyed a free meal; he once located the entire...
 Here are five key questions to ask yourself to ensure your data center design stays on the right track: 1. How many racks do you need? What size are they? The number of racks determines the space in your data center....
Here are five key questions to ask yourself to ensure your data center design stays on the right track: 1. How many racks do you need? What size are they? The number of racks determines the space in your data center....
 At present, the construction mode of using technology to assist urban management has shifted from the previous safe city construction based on video surveillance to the smart city construction based on multi-sensor technology. In this process,...
At present, the construction mode of using technology to assist urban management has shifted from the previous safe city construction based on video surveillance to the smart city construction based on multi-sensor technology. In this process,...
 Smartphones, tablets, laptops, personal PCs, smart lights, smart sockets... More and more devices at home need to connect to WiFi, and these devices are connected through the wireless router in our home....
Smartphones, tablets, laptops, personal PCs, smart lights, smart sockets... More and more devices at home need to connect to WiFi, and these devices are connected through the wireless router in our home....
 Many digital stories show that passwords are becoming a thing of the past and cannot support the trillion-dollar mobile payment market. In 2014, there were 1,500 data leaks worldwide and 1 billion pieces of personal information were stolen....
Many digital stories show that passwords are becoming a thing of the past and cannot support the trillion-dollar mobile payment market. In 2014, there were 1,500 data leaks worldwide and 1 billion pieces of personal information were stolen....
 1 Overview Software testing is a very broad concept. From the perspective of its running through the entire software life cycle, testing can be divided into stages such as module testing, integration testing, and system testing. Testing can also be divided into static checking and...
1 Overview Software testing is a very broad concept. From the perspective of its running through the entire software life cycle, testing can be divided into stages such as module testing, integration testing, and system testing. Testing can also be divided into static checking and...
 The MAXQ3120 electricity meter (EM) reference design builds a multifunction, multirate electricity meter that complies with all applicable standards worldwide....
The MAXQ3120 electricity meter (EM) reference design builds a multifunction, multirate electricity meter that complies with all applicable standards worldwide....
 The rise of smartphones allows us to interact with machines by tapping on touch screens. So what other ways of interaction will humans develop behind this small piece of glass? Will we interact with devices through voice? Or will we wear augmented reality glasses and receive the information we need all day? Or will we use touch......
The rise of smartphones allows us to interact with machines by tapping on touch screens. So what other ways of interaction will humans develop behind this small piece of glass? Will we interact with devices through voice? Or will we wear augmented reality glasses and receive the information we need all day? Or will we use touch......
 The development of face recognition technology in China started in the late 1990s and has gone through five stages: "technology introduction - professional market introduction - technology improvement - technology application - use in various industries and fields". So far, with the continuous maturity of domestic face recognition technology, this technology has been increasingly used......
The development of face recognition technology in China started in the late 1990s and has gone through five stages: "technology introduction - professional market introduction - technology improvement - technology application - use in various industries and fields". So far, with the continuous maturity of domestic face recognition technology, this technology has been increasingly used......
 Big Data Analysis What is Big Data? Big data is usually used to describe a large amount of unstructured or semi-structured data. It takes a lot of money to convert such data into relational data for future analysis. Big data technology is......
Big Data Analysis What is Big Data? Big data is usually used to describe a large amount of unstructured or semi-structured data. It takes a lot of money to convert such data into relational data for future analysis. Big data technology is......
 [2022 Digi-Key Innovation Design Competition] Source code of construction monitoring and security system works
[2022 Digi-Key Innovation Design Competition] Source code of construction monitoring and security system works Research progress of security laser radar
Research progress of security laser radar Smart Security - Comprehensive Analysis and Case Study of Video Surveillance
Smart Security - Comprehensive Analysis and Case Study of Video Surveillance Microwave and millimeter wave security remote sensing technology
Microwave and millimeter wave security remote sensing technology Smart home security integrated solution terminal based on Pingtouge RVB2601 (source code)
Smart home security integrated solution terminal based on Pingtouge RVB2601 (source code) Design and implementation of intelligent security and home service robots
Design and implementation of intelligent security and home service robots Design of Special Fresh Air Fan Controller
Design of Special Fresh Air Fan Controller Loop Design of High PF Flyback Critical Mode Switching Power Supply
Loop Design of High PF Flyback Critical Mode Switching Power Supply MCU program examples, mainly including C language programs for serial port, PWM, AD, SPI, LED, etc.
MCU program examples, mainly including C language programs for serial port, PWM, AD, SPI, LED, etc. VCD power supply circuit of unknown brand machine
VCD power supply circuit of unknown brand machine Power Management Applications Solutions
Power Management Applications Solutions Field Instrumentation Details
Field Instrumentation Details ds1820b temperature measurement program written by me
ds1820b temperature measurement program written by me L298+ optocoupler circuit diagram
L298+ optocoupler circuit diagram Layout of Capacitor and Resist
Layout of Capacitor and Resist Starting of three-phase asynchronous motor
Starting of three-phase asynchronous motor