- ARM helps Entropy Technology's encryption coprocessor IP obtain PSA Certified Level 3 RoT Component certification
-
 Addressing the security subsystem requirements of AIoT chips: Arm helps Entropy Technology's encryption coprocessor IP obtain PSA Certified Level 3 RoT Component certification (Taiwan, October 28, 2024) ...
Addressing the security subsystem requirements of AIoT chips: Arm helps Entropy Technology's encryption coprocessor IP obtain PSA Certified Level 3 RoT Component certification (Taiwan, October 28, 2024) ...
-
Keywords:
ARM
Entropy Technology
Encryption
Coprocessor
IP
PSA
Certification
Publish Time:2024-10-28
- Akamai and Kyndryl announce collaboration to deliver Zero Trust segmentation services to address cybersecurity challenges
-
New Collaboration Helps Customers Accelerate Zero Trust Implementation October 25, 2024 – Akamai Technologies, the cloud service provider responsible for supporting and protecting online life, today announced that it has partnered with the leading cloud computing company to accelerate Zero Trust implementation. ...
-
Keywords:
Akamai
Kyndryl
Zero
Cybersecurity
Publish Time:2024-10-25
- Nordic Semiconductor enables local or remote access for Matter over Wi-Fi smart locks
-
 Anona Security Technology Limited's Anona Holo smart lock integrates the nRF5340 SoC and nRF7002 Wi-Fi 6 companion IC to provide secure Ma ...
Anona Security Technology Limited's Anona Holo smart lock integrates the nRF5340 SoC and nRF7002 Wi-Fi 6 companion IC to provide secure Ma ...
-
Keywords:
Nordic
Matter
Wi-Fi
smart lock
remote access
smart home
Publish Time:2024-08-08
- Build a solid AI engine security line of defense, two major strategies to help developers ensure software development security
-
With the rapid development of artificial intelligence machine learning (AI ML) and large language model (LLM) technology, the field of software development is changing rapidly. According to a recent survey of 1,200 technology experts around the world, ...
-
Keywords:
AI
software development
security
cybersecurity
Publish Time:2024-08-07
- Gartner Publishes Three Major Impacts of Application and Data Localization Strategies on Cybersecurity
-
 Gartner released three major impacts of application and data localization strategies on the cybersecurity of multinational enterprises. According to Gartner's forecast, by 2027, at least 25% of multinational enterprises will have one or more affected ...
Gartner released three major impacts of application and data localization strategies on the cybersecurity of multinational enterprises. According to Gartner's forecast, by 2027, at least 25% of multinational enterprises will have one or more affected ...
-
Keywords:
Gartner
data
localization
cybersecurity
data isolation
Publish Time:2024-07-04
- Akamai's latest SOTI report: Bots account for 42% of total web traffic, and nearly two-thirds are malicious bots
-
Undetected Web Content Scraping Bots Have a Serious Impact on the E-Commerce Industry July 2, 2024 – Akamai Technologies, a cloud service provider responsible for supporting and protecting online life, ...
-
Keywords:
Akamai
SOTI
bot traffic
web traffic
bots
Publish Time:2024-07-02
- Akamai and Digital China work together to expand the enterprise security market and build a security ecosystem
-
Akamai Announces China's First Enterprise Security Distribution PartnerJune 11, 2024 – As a cloud service provider that supports and protects online life, Akamai Technologies ...
-
Keywords:
Akamai
Digital China
Enterprise Security
Security
Ecosystem
Publish Time:2024-06-11
- IoT empowers industrial production maintenance and safety
-
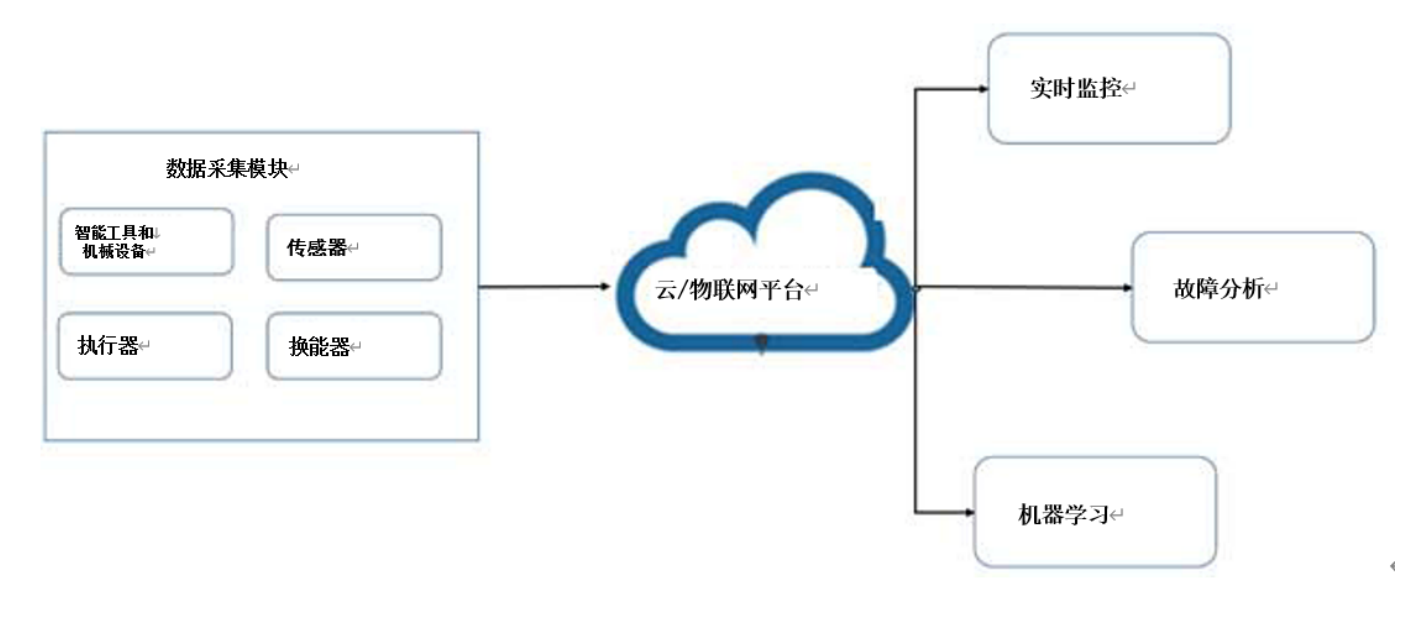 The continued demand for sustainability and greater efficiency has spurred innovation in the field of industrial automation. The Internet of Things allows advanced technologies to be rapidly integrated into industrial automation. Smart, fully connected factories allow manufacturers to provide ...
The continued demand for sustainability and greater efficiency has spurred innovation in the field of industrial automation. The Internet of Things allows advanced technologies to be rapidly integrated into industrial automation. Smart, fully connected factories allow manufacturers to provide ...
-
Keywords:
Internet of Things
Industrial Production
Maintenance
Security
Publish Time:2024-06-03
- Lenovo Nettop launches "1110 Emergency Disaster Recovery Integrated Solution" to build a solid data security barrier for enterprises and organizations
-
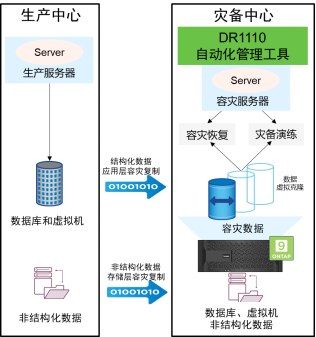 Beijing, China, May 23, 2024 - Lenovo Linksys, a leading intelligent data management solutions and services provider dedicated to helping Chinese companies and organizations unleash the potential of data and accelerate digital transformation ...
Beijing, China, May 23, 2024 - Lenovo Linksys, a leading intelligent data management solutions and services provider dedicated to helping Chinese companies and organizations unleash the potential of data and accelerate digital transformation ...
-
Keywords:
Lenovo Lingtuo
emergency
disaster recovery
data security
Publish Time:2024-05-23
- JFrog Global Software Supply Chain Development Report Finds Most Vulnerabilities Rated “Critical” Are Misleading
-
74% of CVSS ratings classified as “High” or “Critical” are not applicable in most common cases, yet 60% of security and development teams still spend 25% of their time fixing these vulnerabilities May 21, 2024 ...
-
Keywords:
JFrog
software
supply chain
vulnerabilities
Publish Time:2024-05-21
- JFrog Research: Docker Hub Underwent Coordinated Attack, Implanting Millions of Malicious Repositories
-
 JFrog and Docker have teamed up to take mitigation and cleanup actions after recently discovering that the Docker Hub repository was used to spread malware and phishing scams. By: Security Researcher Andrey ...
JFrog and Docker have teamed up to take mitigation and cleanup actions after recently discovering that the Docker Hub repository was used to spread malware and phishing scams. By: Security Researcher Andrey ...
-
Keywords:
JFrog
Docker
attack
repository
software ecosystem
Publish Time:2024-04-30
- BICS blocks €87 million fraud attack
-
 In 2023, BICS blocked 50.7 billion spam and automated voice calls, up from 39.5 billion SMS phishing attacks in 2022. The trend is on the rise, with BICS blocking 47.3 billion SMS phishing attacks worldwide. ...
In 2023, BICS blocked 50.7 billion spam and automated voice calls, up from 39.5 billion SMS phishing attacks in 2022. The trend is on the rise, with BICS blocking 47.3 billion SMS phishing attacks worldwide. ...
-
Keywords:
BICS
fraud attack
fraud
prevention
security
Publish Time:2024-04-25
- World Backup Day | How to prevent the ever-changing threats of ransomware and protect data security?
-
As data becomes increasingly the driving force of corporate business, protecting data from loss, damage, and theft becomes more important and has risen to the top of the list of concerns for corporate executives. ...
-
Keywords:
World Backup Day
Ransomware
Data Security
Publish Time:2024-03-29
- Entropy Technology launches the next-generation cryptographic coprocessor PUFcc7, which significantly improves computing performance and supports the latest communication protocol TLS 1.3
-
 (Hsinchu, Taiwan, March 28) PUFsecurity, a company dedicated to developing chip security solutions with Physical Unclonable Function (PUF) as its core technology, today announced the launch of a new generation of encryption protocol ...
(Hsinchu, Taiwan, March 28) PUFsecurity, a company dedicated to developing chip security solutions with Physical Unclonable Function (PUF) as its core technology, today announced the launch of a new generation of encryption protocol ...
-
Keywords:
Entropy Technology
encryption
coordination
processor
PUFcc7
computing performance
communication protocol
Publish Time:2024-03-28
- Akamai's latest SOTI report: APJ manufacturing industry suffers the most API cyberattacks
-
According to the latest Akamai SOTI research report, the manufacturing industry in APJ has become the industry that suffers the most from API attacks, accounting for nearly one-third (31.2%) of the total. ...
-
Keywords:
Akamai
SOTI
:APJ
manufacturing
API
cyberattack
Publish Time:2024-03-27
- Nordic Semiconductor supports CSA IoT Device Security Specification 1.0 and certification program
-
 Supporting the CSA initiative demonstrates Nordic Semiconductor's continued commitment to providing customers with the security features they need to develop IoT products that comply with IoT device security specifications. Oslo, Norway – 20 ...
Supporting the CSA initiative demonstrates Nordic Semiconductor's continued commitment to providing customers with the security features they need to develop IoT products that comply with IoT device security specifications. Oslo, Norway – 20 ...
-
Keywords:
Nordic
CSA
Internet of Things
safety regulations
certification
Publish Time:2024-03-25
- Akamai launches new features for App & API Protector to strengthen security defenses and simplify operations
-
Enhancements include Layer 7 DDoS protection and advanced machine learning capabilities March 13, 2024 – Akamai Technologies, the cloud service provider responsible for supporting and protecting life online ...
-
Keywords:
Akamai
API
security defense
machine learning
Publish Time:2024-03-13
- Solid as a rock, guarded by security
-
 With the widespread application of chips and Internet cloud technology in various industries, information security has become increasingly important. Nowadays, every aspect of people’s daily life is closely related to chips and Internet cloud technology. ...
With the widespread application of chips and Internet cloud technology in various industries, information security has become increasingly important. Nowadays, every aspect of people’s daily life is closely related to chips and Internet cloud technology. ...
-
Keywords:
Ambarella
Ambarella
information security
Publish Time:2024-03-05
- Infineon OPTIGA Trust M MTR: Simplifying Matter security certification and protecting privacy
-
 With the smart home market growing strongly, installations of smart home devices are expected to surge by 35% over the next five years. However, behind the vigorous development of the market, there are also some problems that need to be solved urgently. mutual ...
With the smart home market growing strongly, installations of smart home devices are expected to surge by 35% over the next five years. However, behind the vigorous development of the market, there are also some problems that need to be solved urgently. mutual ...
-
Keywords:
Infineon
Matter
Publish Time:2024-02-27
- MIT develops new tag tamper-proof technology
-
A few years ago, researchers at MIT successfully developed an encrypted ID tag. Compared with traditional radio frequency tags (RFID), this kind of tag is smaller, more affordable and more secure. it ...
-
Keywords:
Label
Publish Time:2024-02-21
Open Source Project Recommendations
Latest Internet of Things Articles
MorePopular Resource Recommendations
MorePopular Headline Technical Articles
MorePotentially Interesting Components
MorePopular Download Recommendations
 Anona Security Technology Limited's Anona Holo smart lock integrates the nRF5340 SoC and nRF7002 Wi-Fi 6 companion IC to provide secure Ma ...
Anona Security Technology Limited's Anona Holo smart lock integrates the nRF5340 SoC and nRF7002 Wi-Fi 6 companion IC to provide secure Ma ...
 Gartner released three major impacts of application and data localization strategies on the cybersecurity of multinational enterprises. According to Gartner's forecast, by 2027, at least 25% of multinational enterprises will have one or more affected ...
Gartner released three major impacts of application and data localization strategies on the cybersecurity of multinational enterprises. According to Gartner's forecast, by 2027, at least 25% of multinational enterprises will have one or more affected ...
 The continued demand for sustainability and greater efficiency has spurred innovation in the field of industrial automation. The Internet of Things allows advanced technologies to be rapidly integrated into industrial automation. Smart, fully connected factories allow manufacturers to provide ...
The continued demand for sustainability and greater efficiency has spurred innovation in the field of industrial automation. The Internet of Things allows advanced technologies to be rapidly integrated into industrial automation. Smart, fully connected factories allow manufacturers to provide ...
 Beijing, China, May 23, 2024 - Lenovo Linksys, a leading intelligent data management solutions and services provider dedicated to helping Chinese companies and organizations unleash the potential of data and accelerate digital transformation ...
Beijing, China, May 23, 2024 - Lenovo Linksys, a leading intelligent data management solutions and services provider dedicated to helping Chinese companies and organizations unleash the potential of data and accelerate digital transformation ...
 JFrog and Docker have teamed up to take mitigation and cleanup actions after recently discovering that the Docker Hub repository was used to spread malware and phishing scams. By: Security Researcher Andrey ...
JFrog and Docker have teamed up to take mitigation and cleanup actions after recently discovering that the Docker Hub repository was used to spread malware and phishing scams. By: Security Researcher Andrey ...
 In 2023, BICS blocked 50.7 billion spam and automated voice calls, up from 39.5 billion SMS phishing attacks in 2022. The trend is on the rise, with BICS blocking 47.3 billion SMS phishing attacks worldwide. ...
In 2023, BICS blocked 50.7 billion spam and automated voice calls, up from 39.5 billion SMS phishing attacks in 2022. The trend is on the rise, with BICS blocking 47.3 billion SMS phishing attacks worldwide. ...
 (Hsinchu, Taiwan, March 28) PUFsecurity, a company dedicated to developing chip security solutions with Physical Unclonable Function (PUF) as its core technology, today announced the launch of a new generation of encryption protocol ...
(Hsinchu, Taiwan, March 28) PUFsecurity, a company dedicated to developing chip security solutions with Physical Unclonable Function (PUF) as its core technology, today announced the launch of a new generation of encryption protocol ...
 Supporting the CSA initiative demonstrates Nordic Semiconductor's continued commitment to providing customers with the security features they need to develop IoT products that comply with IoT device security specifications. Oslo, Norway – 20 ...
Supporting the CSA initiative demonstrates Nordic Semiconductor's continued commitment to providing customers with the security features they need to develop IoT products that comply with IoT device security specifications. Oslo, Norway – 20 ...
 With the widespread application of chips and Internet cloud technology in various industries, information security has become increasingly important. Nowadays, every aspect of people’s daily life is closely related to chips and Internet cloud technology. ...
With the widespread application of chips and Internet cloud technology in various industries, information security has become increasingly important. Nowadays, every aspect of people’s daily life is closely related to chips and Internet cloud technology. ...
 With the smart home market growing strongly, installations of smart home devices are expected to surge by 35% over the next five years. However, behind the vigorous development of the market, there are also some problems that need to be solved urgently. mutual ...
With the smart home market growing strongly, installations of smart home devices are expected to surge by 35% over the next five years. However, behind the vigorous development of the market, there are also some problems that need to be solved urgently. mutual ...
 Research on security vulnerability detection technology of multi-source heterogeneous data in the Internet of Things
Research on security vulnerability detection technology of multi-source heterogeneous data in the Internet of Things IoT device identification method integrating multimodal IoT device fingerprint and ensemble learning_Lu Xulin
IoT device identification method integrating multimodal IoT device fingerprint and ensemble learning_Lu Xulin Analysis of key nodes of satellite Internet of Things integrating functional characteristics and topological structure
Analysis of key nodes of satellite Internet of Things integrating functional characteristics and topological structure Design and implementation of agricultural data monitoring Internet of Things system
Design and implementation of agricultural data monitoring Internet of Things system Design of remote controlled automatic irrigation and sprinkler system based on Internet of Things technology
Design of remote controlled automatic irrigation and sprinkler system based on Internet of Things technology Aviation obstacle avoidance light control system based on Internet of Things technology_Liu Xinyu
Aviation obstacle avoidance light control system based on Internet of Things technology_Liu Xinyu Design of bus controller for enterprise distributed control system
Design of bus controller for enterprise distributed control system A JMS messaging middleware similar to openJMS distributed under ObjectWeb.
A JMS messaging middleware similar to openJMS distributed under ObjectWeb. W78E51/W78E51B, Chinese data, pdf datasheet (8-bit microcontroller with wide frequency range and low power consumption)
W78E51/W78E51B, Chinese data, pdf datasheet (8-bit microcontroller with wide frequency range and low power consumption) [资料]-JIS T3258-2012 Sterile epidural catheters for single use.pdf
[资料]-JIS T3258-2012 Sterile epidural catheters for single use.pdf Cable interlayer cable fire protection design and construction
Cable interlayer cable fire protection design and construction USB-BLASTER Schematic
USB-BLASTER Schematic IPC-TM-650,2,3,4,2a.pdf
IPC-TM-650,2,3,4,2a.pdf Application of state machine thinking in single chip microcomputer programming
Application of state machine thinking in single chip microcomputer programming Leon3 & GPLIB libraries for CYGWIN/UNIX
Leon3 & GPLIB libraries for CYGWIN/UNIX Serial port detection program written in verilogHDL
Serial port detection program written in verilogHDL