Purpose: Encrypt embedded code programs running on STM32
Compilation environment: IAR Embedded System for ARM5.5
1. STM32Flash organization
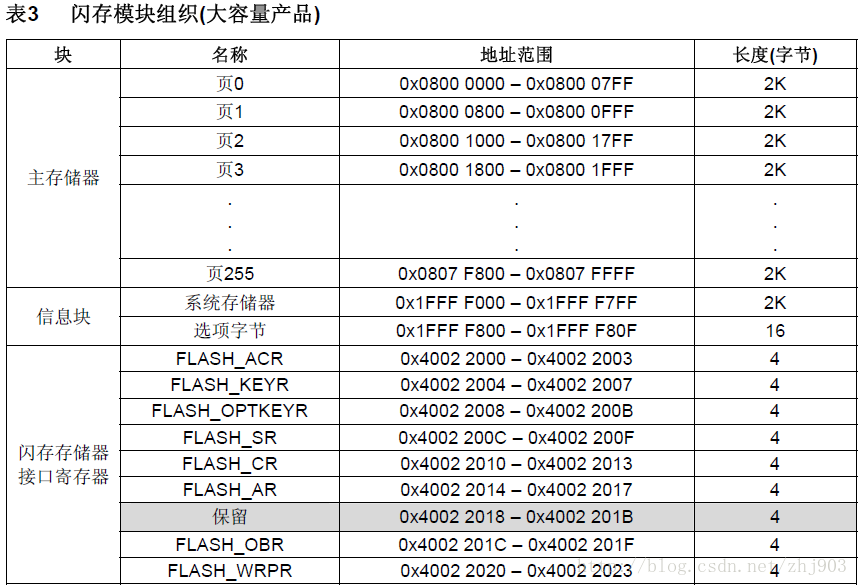
The Flash of STM32 includes main memory (HD version, 512KB) + information block. The information block includes 2KB system memory (for system bootstrap startup code) and 16 bytes of option bytes (8 bytes of data + 8 bytes of data inverse code).
2. STM32 read protection
STM32 read protection is started by setting the RDP option byte and then resetting the system to load the new RDP option byte. After the protection byte is written with the corresponding value:
●Access to the main flash memory by executing code from the built-in SRAM or FSMC, access to the flash memory through DMA1, DMA2, JTAG, SWV (Serial Wire Viewer), SWD (Serial Wire Debug), ETM and boundary scan will be prohibited.
●Only read operations on the main Flash memory are allowed from user code (booting from the main Flash memory in non-debug mode).
●Pages 0 to 3 (small-capacity and medium-capacity products) or pages 0 to 1 (large-capacity and interconnected products) are automatically write-protected. The rest of the memory can be programmed by the code executed in the main flash memory (to implement functions such as IAP or data storage), but write or erase operations (except for full-chip erase) are not allowed in debug mode or after booting from the internal SRAM.
●All functions of loading code to the built-in SRAM and executing code via JTAG/SWD are still valid, and it is also possible to boot from the built-in SRAM via JTAG/SWD. This function can be used to remove the read protection. When the read protection option byte is changed to the value of the memory unprotected, the whole chip erase process will be executed.
●You can use the system startup program to remove the read protection (at this time, you only need to perform a system reset to reload the option bytes), and the chip will automatically erase all the contents of the Flash.
3. STM32 encryption
1. Use the system startup program STM32 Flash Loader demonstrator to set the Flash to read protection.
All access operations to the main memory by debugging tools, built-in SRAM or FSMC execution code will be prohibited, and only user code can read and program the main Flash memory (except the 4KB area at the beginning of the Flash cannot be programmed). User code allows autonomous programming to achieve functions such as IAP or data storage.
In this way, the cracker will not be able to read the code in the Flash using debugging tools, built-in SRAM or FSMC code execution, etc. The cracker also cannot use the system startup program to read the code, because to remove the read protection, the entire chip must be erased.
2. Use device ID protection in the main program
Even if the Flash is set to read protection, hackers can download their own small program through IAP to read the contents of the Flash. Therefore, it is also necessary to use the unique ID of the device for encryption protection. In the main program, add a check for the unique ID of the device, so that even if the hacker reads the binary code in the chip, he cannot use this binary code to copy a new device. Specific implementation method:
(1) Define a (32-bit or more) const variable in the application program, and set the variable value to 0xFF. Each time the program is started, check the value of the const variable. If it is all 0xFF, read the unique ID of the device and write it to the const variable through Flash programming (because it is all 0xFF, it can be programmed).
(2) Check const variables in multiple places in the program. If the variable value is not 0xFF and is inconsistent with the device ID, execute code that is not related to the function (such as self-erase).
In this way, even if the cracker reads the binary code in the chip, it cannot be copied to other chips because the binary code contains the device's unique ID and is unique.
In order to prevent crackers from using disassembly to find the location of the same data in the binary file based on the chip ID data and crack it, the ID can be split into different combinations and written to different and non-contiguous places. Furthermore, multiple copies of such scattered IDs can be detected in the program to increase the difficulty of disassembly. Alternatively, the CPUID can be encrypted and the encrypted result can be stored in Flash.
4. Implementation of program encryption
//Encrypted CPUID
volatile const static uint32 CPUIDEncrypt = 0xFFFFFFFF;
//Write encrypted data
void WriteEncrypt(void)
{
//First time programming: write UID into Flash
if(CPUIDEncrypt==0xFFFFFFFF)
{
uint32_t CpuID[3];
//Get the unique ID of the CPU
CpuID[0]=*(vu32*)(UID_BASE);
CpuID[1]=*(vu32*)(UID_BASE+4);
CpuID[2]=*(vu32*)(UID_BASE+8);
//Encryption algorithm, very simple encryption algorithm
uint32_t EncryptCode=(CpuID[0]>>3)+(CpuID[1]>>1)+(CpuID[2]>>2);
FLASH_Unlock();
FLASH_ClearFlag(FLASH_FLAG_BSY|FLASH_FLAG_EOP|FLASH_FLAG_PGERR|FLASH_FLAG_WRPRTERR);
FLASH_ProgramWord((uint32_t)&CPUIDEncrypt, EncryptCode);
FLASH_Lock();
}
}
//Judge encryption
bool JudgeEncrypt(void)
{
uint32_t CpuID[4];
//Get the unique ID of the CPU
CpuID[0]=*(vu32*)(UID_BASE);
CpuID[1]=*(vu32*)(UID_BASE+4);
CpuID[2]=*(vu32*)(UID_BASE+8);
//Encryption algorithm, very simple encryption algorithm
CpuID[3]=(CpuID[0]>>3)+(CpuID[1]>>1)+(CpuID[2]>>2);
// Check if the UID in Flash is legal
return (CPUIDEncrypt == CpuID[3]);
}
1. Separate the two functions of writing encrypted data and judging encryption. Writing encryption is at the beginning of PrsCtrlTask, while judging encryption is distributed to every corner of the program.
2. It is very important that the definition of the CPUID encrypted value must be added with the "volatile" type:
volatile const static uint32 CPUIDEncrypt = 0xFFFFFFFF;
Otherwise, the program is compiled for speed optimization and will not re-read the encrypted value when judging the encrypted value, resulting in incorrect judgment.
3. In the project options Options->Debugger->Download, select: use flash loader
Otherwise, Flash programming in the main program will fail.
Previous article:A preliminary study on the STM32F4 clock system (Part 2)
Next article:Application protection method based on STM32F103 ID number
- Popular Resources
- Popular amplifiers
- Learn ARM development(16)
- Learn ARM development(17)
- Learn ARM development(18)
- Embedded system debugging simulation tool
- A small question that has been bothering me recently has finally been solved~~
- Learn ARM development (1)
- Learn ARM development (2)
- Learn ARM development (4)
- Learn ARM development (6)
 Professor at Beihang University, dedicated to promoting microcontrollers and embedded systems for over 20 years.
Professor at Beihang University, dedicated to promoting microcontrollers and embedded systems for over 20 years.
- LED chemical incompatibility test to see which chemicals LEDs can be used with
- Application of ARM9 hardware coprocessor on WinCE embedded motherboard
- What are the key points for selecting rotor flowmeter?
- LM317 high power charger circuit
- A brief analysis of Embest's application and development of embedded medical devices
- Single-phase RC protection circuit
- stm32 PVD programmable voltage monitor
- Introduction and measurement of edge trigger and level trigger of 51 single chip microcomputer
- Improved design of Linux system software shell protection technology
- What to do if the ABB robot protection device stops
- Detailed explanation of intelligent car body perception system
- How to solve the problem that the servo drive is not enabled
- Why does the servo drive not power on?
- What point should I connect to when the servo is turned on?
- How to turn on the internal enable of Panasonic servo drive?
- What is the rigidity setting of Panasonic servo drive?
- How to change the inertia ratio of Panasonic servo drive
- What is the inertia ratio of the servo motor?
- Is it better for the motor to have a large or small moment of inertia?
- What is the difference between low inertia and high inertia of servo motors?
- What domestic chips are needed to DIY a fast-charging chromium iron or an electric chromium iron that works as a laptop power supply?
- Bluetooth module communicates with mobile phone
- The compilation of the program sent by serial communication always fails
- Does the clearance below the crystal oscillator refer to the layer where the chip is located or all layers?
- [Automatic clock-in walking timing system based on face recognition] Maixbit K210 initialization loading SD card unstable problem
- How to control three colorful LED light strips with the same signal using three remote controllers
- Electromagnetic compatibility circuit board design: based on Altium Designer platform
- Make driving fun! Designing interactive and non-distracting infotainment systems
- How to select external clock for TI DSP?
- Lecture 2 Introduction to SOPC development process and development platform.pdf

 INA200AIDGKRG4ACTIVE
INA200AIDGKRG4ACTIVE
















 京公网安备 11010802033920号
京公网安备 11010802033920号