Keyless entry systems are a basic feature of most modern cars. The biggest advantage is convenience, as the vehicle detects the key and unlocks the car automatically. However, many people question the security of such systems. They believe that the convenience of keyless entry systems sometimes comes at a price: information security.
This article explains how hackers attack key fobs and the proactive security measures Synopsys recommends.
Over the years, security researchers have discovered many vulnerabilities in automotive systems. As a result, the demand for automotive cybersecurity has risen. A recent high-profile case is a series of vulnerabilities in the keyless entry system of the Tesla Model X in November 2020. The vulnerability was discovered by Lennert Wouters of the University of Leuven in Belgium.
Steps in a key fob attack
The operating steps of the Tesla Model X keyless entry system are shown in the figure. The numbers in the figure represent the steps. Please note that the target vehicle is locked and the target key card is away from the vehicle.
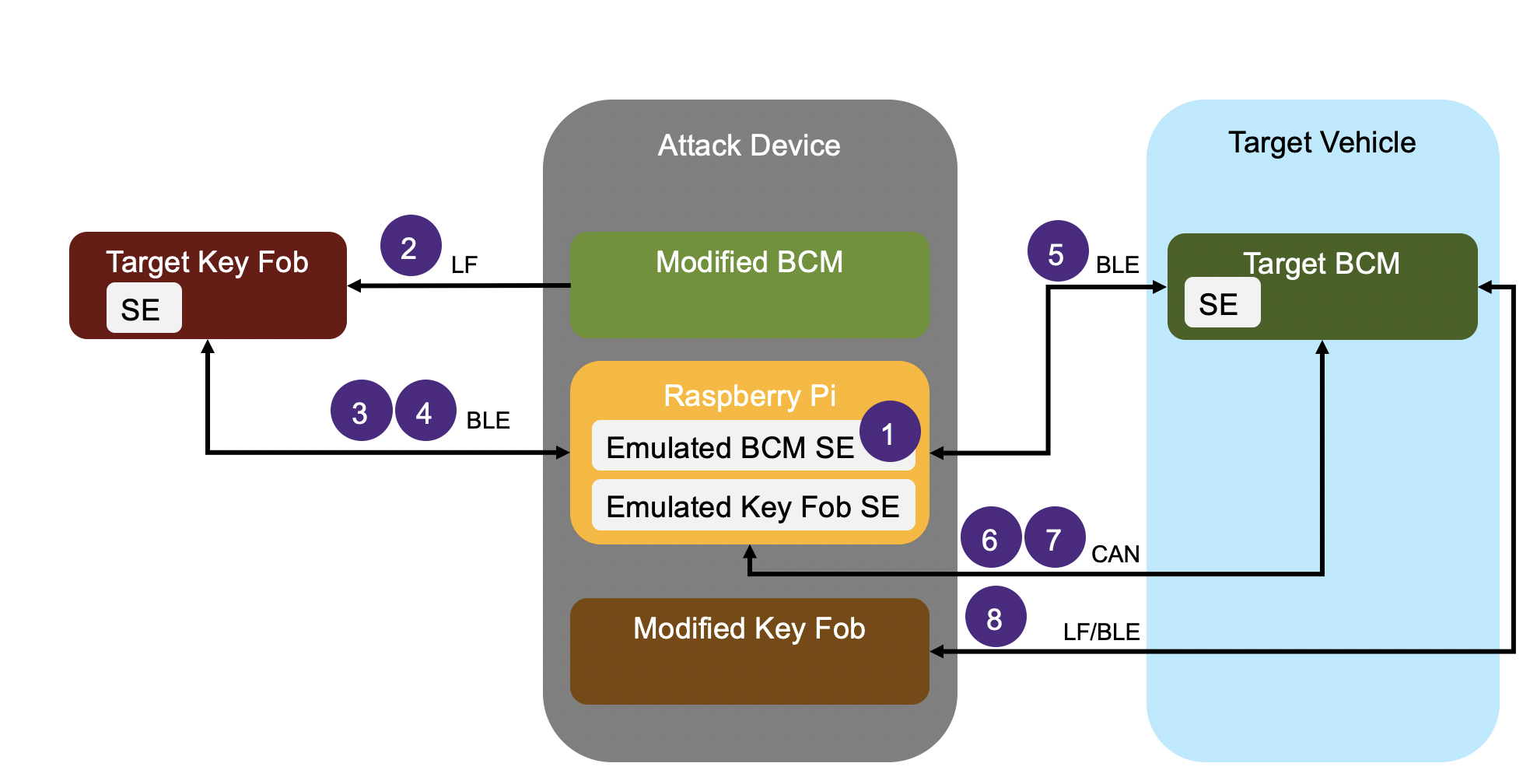
1. The attacker approaches the target vehicle, reads the vehicle identification number (VIN) through the windshield, and configures the emulated SE for the modified body controller (BCM) in the attack device to use the target VIN
2. The attacker finds the target key fob and brings the attack device close to it and pretends to be the target vehicle, connecting via low frequency (LF) at a distance of about 5 meters. The attacker uses an identifier derived from the VIN to force the previously paired target key fob to appear as connectable via Bluetooth Low Energy (BLE)
3. The attacker uses a Raspberry Pi to push a malicious firmware update to the target key fob via BLE to gain full control of the key fob. This update can be performed by using the over-the-air download service (OTA) on the target key fob at a distance of up to 30 meters.
4. After updating the target key fob, the attack device will reconnect via BLE. Since the key fob is running malicious firmware controlled by the attacker, which allows arbitrary Application Protocol Data Unit (APDU) commands to be sent to the SE in the target key fob, the attacker is able to extract many valid one-time unlock commands (e.g. unlock doors, trunk, etc.) from the SE in the smart key to the target vehicle.
5. The attacker approaches the target vehicle and uses a valid unlock command to unlock the target vehicle. The unlock command is sent from the Raspberry Pi to the target BCM via BLE
6. The attacker has physical access to the interior of the vehicle and can physically connect the attack device to the vehicle network through the diagnostic port located below the central display. The attack device connects to the target BCM via the controller area network (CAN)
7. The attacking device instructs the target BCM to pair with the modified key fob. After passing the BCM challenge response verification, the modified key fob is added and the necessary credentials are stored in the emulated SE of the key fob
8. The attacker starts the vehicle using the newly paired key fob on the attack device, successfully passes the challenge-response authentication using the credentials previously stored in the simulated key fob SE, and then drives away with the target vehicle
Vulnerabilities/Flaws that Make Key Fobs Vulnerable
This type of attack is mainly caused by the following two vulnerabilities/flaws:
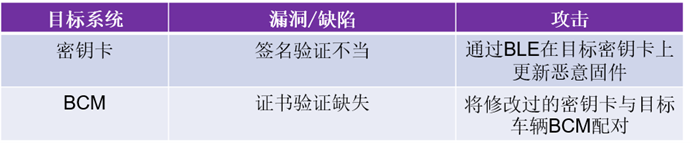
Although signature verification is performed on the key fob, due to the vulnerability, an attacker can update the key fob with malicious firmware via BLE. In addition, although a valid key fob usually stores the signature certificates received from the backend, these certificates are not verified by the vehicle BCM when paired with the key fob.
It is worth noting that the security researchers responsibly disclosed these issues to Tesla in August 2020. Tesla released an OTA patch in November 2020.
Use application security testing tools to address execution and design vulnerabilities/defects
In the first case, improper key card signature verification, this type of problem can usually be discovered using static application security testing, software composition analysis (identifying known vulnerabilities) and fuzz testing (detecting unknown vulnerabilities). In addition, penetration testing that focuses on high-risk areas, such as security-related functions and firmware updates, can also detect such vulnerabilities.
The second case is the lack of certificate verification in the pairing protocol design between the BCM and the key fob. These types of design issues can usually be identified through a security design review. In addition, a proper threat analysis and risk assessment must be performed on the target system to identify high-risk areas, which helps define appropriate security requirements and design corresponding security controls.
There are already many initiatives in the automotive industry to help improve cybersecurity, such as the ISO SAE 21434 cybersecurity engineering standard and UN Regulation 155 on cybersecurity and cybersecurity management systems.
Developing 100% secure automotive systems is not realistic, so automotive companies need to consider and deploy appropriate measures to enable OTA updates to patch newly discovered vulnerabilities in a timely manner.
Previous article:How Car Keyless Entry Systems Can Be Hacked
Next article:INRIX Launches Cloud-Based Smart Alerts to Improve Driving Safety
- Popular Resources
- Popular amplifiers
- 2024 China Automotive Charging and Battery Swapping Ecosystem Conference held in Taiyuan
- State-owned enterprises team up to invest in solid-state battery giant
- The evolution of electronic and electrical architecture is accelerating
- The first! National Automotive Chip Quality Inspection Center established
- BYD releases self-developed automotive chip using 4nm process, with a running score of up to 1.15 million
- GEODNET launches GEO-PULSE, a car GPS navigation device
- Should Chinese car companies develop their own high-computing chips?
- Infineon and Siemens combine embedded automotive software platform with microcontrollers to provide the necessary functions for next-generation SDVs
- Continental launches invisible biometric sensor display to monitor passengers' vital signs
- Intel promotes AI with multi-dimensional efforts in technology, application, and ecology
- ChinaJoy Qualcomm Snapdragon Theme Pavilion takes you to experience the new changes in digital entertainment in the 5G era
- Infineon's latest generation IGBT technology platform enables precise control of speed and position
- Two test methods for LED lighting life
- Don't Let Lightning Induced Surges Scare You
- Application of brushless motor controller ML4425/4426
- Easy identification of LED power supply quality
- World's first integrated photovoltaic solar system completed in Israel
- Sliding window mean filter for avr microcontroller AD conversion
- What does call mean in the detailed explanation of ABB robot programming instructions?
- STMicroelectronics discloses its 2027-2028 financial model and path to achieve its 2030 goals
- 2024 China Automotive Charging and Battery Swapping Ecosystem Conference held in Taiyuan
- State-owned enterprises team up to invest in solid-state battery giant
- The evolution of electronic and electrical architecture is accelerating
- The first! National Automotive Chip Quality Inspection Center established
- BYD releases self-developed automotive chip using 4nm process, with a running score of up to 1.15 million
- GEODNET launches GEO-PULSE, a car GPS navigation device
- Should Chinese car companies develop their own high-computing chips?
- Infineon and Siemens combine embedded automotive software platform with microcontrollers to provide the necessary functions for next-generation SDVs
- Continental launches invisible biometric sensor display to monitor passengers' vital signs
- 220V AC to 18V DC
- DSPF28335 Study Notes
- Anyone know what component this is?
- 【AT-START-F425 Review】-Recording the use of CAN communication
- HDI blind hole design, did you notice this detail?
- EEWORLD University Hall----Design of DC power supply system for battery testing equipment
- Topic: High-performance dimming electronic ballast solution, a product jointly developed by IXYS and Atmel
- DM368 Development--IPNC Setting Process
- 【TI recommended course】#Give old motors new skills#
- This is a brain teaser - hypotenuse, leg, chord, even Pythagorean theorem

 TC52N2832ECTRT
TC52N2832ECTRT















 京公网安备 11010802033920号
京公网安备 11010802033920号