In October 2017, Arm launched the PSA (Platform Security Architecture) platform security architecture for IoT security, with the vision of protecting the security of trillions of connected devices in the future.
Rob Coombs, director of Arm's emerging business unit, said at the Arm PSA Security Architecture Technology Seminar held in Beijing recently: "There are currently 8 billion IoT devices in the world. With the vigorous development of the IoT industry, it is expected that the number of IoT devices will increase from 8 billion to 24 billion in three years. In the next six years, the IoT will have a huge business opportunity in the fields of chips, software and product equipment. Arm believes that with the rapid development of IoT, 5G and AI technology, the fifth wave of global computing will usher in great opportunities. Arm's vision is to achieve 1 trillion IoT devices by 2035."

Rob Coombs, Director of Emerging Business Unit, Arm
IoT security is urgent.
With the development of the Internet of Things, the number of connected devices deployed has increased in recent years, which has led to a sharp increase in the number of attacks against the Internet of Things. These attacks highlight a very real need: to provide more effective security measures for the entire value chain of connected devices. This value chain includes infrastructure such as energy facilities and connected vehicles, as well as low-cost devices such as network cameras and smart lighting. Security vulnerabilities bring many problems to IoT connected devices. Leakage of confidential information, theft of personal data, loss of control of connected systems, and shutdown of critical infrastructure are all high-risk areas.
The rapid development of IoT services is based on the increasing variety of devices connected to the Internet, such as sensors, actuators or gateways. However, not all of these devices are high-value and high-specification, and a large part of them are small and low-cost devices. Nevertheless, some high-profile attacks that occur frequently have shown that even low-cost devices must be secured because they are likely to become the entry point for hackers to attack large systems. In short, the number of connected assets on the Internet of Things is increasing, and the attack surface for hackers is also expanding. Therefore, more powerful and scalable defense systems are needed.
Rob said that mobile phones are now very secure connected products. The most important reasons are: the attention of mobile phone brands, only a few chip suppliers, limited operating system manufacturers and OTA upgrade service providers, a security architecture based on "security components", an ecosystem realized through high-quality open source software, and OEMs' understanding of chip suppliers and OS suppliers' solutions.

However, the IoT market is a severely fragmented market, from chip suppliers to OEMs, from open source software to OTA.
But Rob also believes that the IoT is many times larger than the mobile market, so despite many difficulties, Arm has been committed to bringing better security to the market.
Given the fragmentation of the IoT field, it is difficult to have an effective and comprehensive security protection mechanism.
PSA certification fills the gap in the industry.
The platform security architecture is a whole composed of threat models, security analysis, and hardware and firmware architecture specifications. PSA provides a framework based on industry best practices, through which consistent security design can be achieved at the hardware and firmware levels. It provides common rules and a more economical method for making more secure devices.
When PSA was first launched, Arm gave three parts of the framework, as follows:
1. Analysis: Sort out specific device security requirements based on potential attack risks.
2. Architecture: Arm provides hardware and firmware related documents, including the necessary security requirements for designing secure devices.
3. Implementation: Arm provides open source reference firmware code for the operating group security area. TF-M is a firmware code that complies with the PSA specification and supports Cortex-M series CPU devices.
4. Certification:
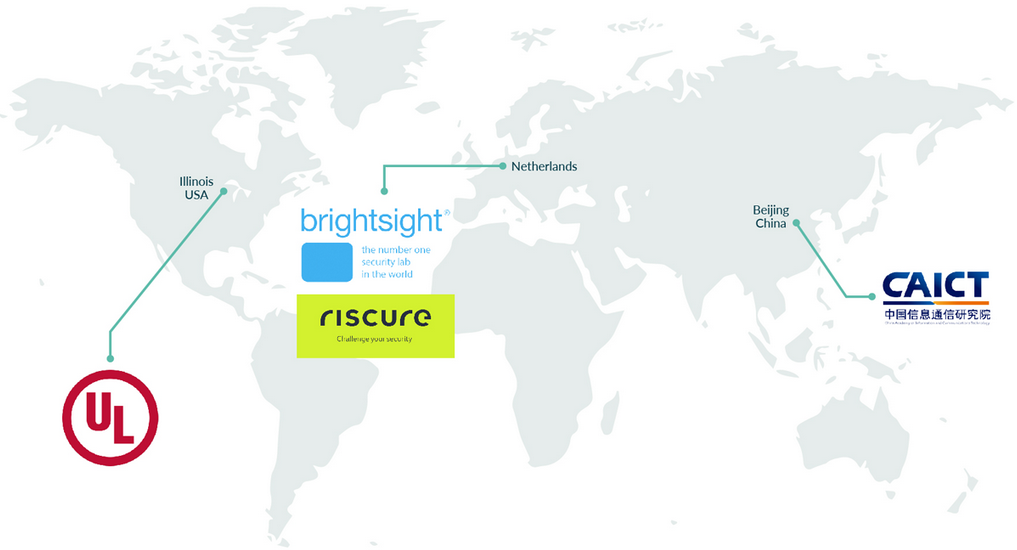
Starting in February 2019, Arm launched the fourth phase of PSA, which is PSA certification. This is the latest part of the PSA framework. It is a certification project jointly launched by Arm and independent security testing laboratories such as Brightsight, China Academy of Information and Communications Technology Terminal Laboratory, Riscure and UL, and consulting agency Prove & Run to support the large-scale deployment of secure IoT solutions based on the Platform Security Architecture (PSA) framework. Through independent security testing, the PSA certification project can help IoT solution developers and device manufacturers establish security and authenticity for data from a wide variety of IoT devices.
As Arm officials said, "It's hard to know how robust a product or device is, or how thorough the security testing is, which makes it difficult to decide which product or device to choose. Many IoT products do not have independent evaluations, which can lead to untrustworthy Internet devices and data. This is exactly the challenge that PSA certification aims to solve: to conduct effective security testing on IoT devices and overcome the huge obstacles that hinder the growth of the Internet of Things. PSA certification provides evaluation solutions for chips, software, and devices that use the PSA architecture and PSA root of trust (RSA-RoT). It will help address the fragmentation of the industry chain and simplify the marketization process for chip vendors, operating systems, middleware developers, OEMs, and system integrators. "
The PSA certification project provides a simple and comprehensive approach to security testing. The certification consists of two parts: a multi-level security robustness solution and an API test suite designed for developers. Security testing is evaluated by a third-party laboratory, independently checking the common parts of the IoT platform, including the PSA root of trust (the root of trust is the root of integrity and confidentiality), the real-time operating system (RTOS), and the device itself.
Rob said that PSA's root of trust is the foundation of everything, so the first phase of PSA locked in chip partners. Chip manufacturers have large shipments and are able and willing to pay for security features, so for the downstream of the industry chain, the time or certification costs they have to bear will be relatively small. With such a good foundation, the next step will be to conduct PSA-related certification for RTOS, OEM, device manufacturers and even cloud service providers. 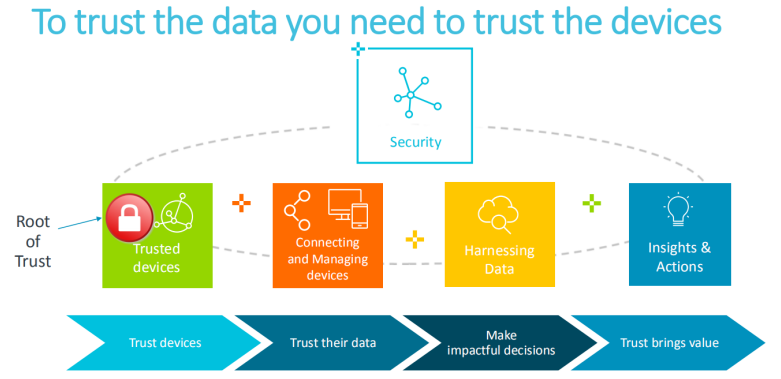
Starting from the underlying chip to the device, data and processing, only when the most basic units achieve security can better security be achieved in the upper layers.
The PSA certification project uses three progressive security levels to ensure that the required security is obtained for its application scenarios. For example, the security robustness required for a temperature sensor deployed in an open-air environment (Level 1) may be different from that deployed in a home environment (Level 2) or an industrial plant (Level 3). After testing, all PSA-certified devices will receive an electronically signed report card (certificate) to determine the security level that can be achieved, providing a basis for enterprises and cloud service providers to make risk-based decisions.
In the field of IoT security, Arm has been working hard
In addition to the Cortex-R processors that have been launched for real-time safety, in 2016, Arm also launched the Cortex-M23/M33 processors for the field of IoT security. Based on Arm's latest ARMv8-M architecture, compared with the previous generation of ARMv7-M architectures such as Cortex-M0/0+, Cortex-M3, Cortex-M4 and Cortex-M7, the new architecture introduces TrustZone technology. By creating independent trusted and untrusted states in the entire processor system, TrustZone can ensure the security of data, firmware and peripherals.
In TrustZone technology, there is a hardware encryption/acceleration technology called Cryptocell. In July 2015, ARM acquired Israeli IoT security network expert Sansa (formerly Discretix) and acquired Cryptocell technology. ARM integrated Cryptocell with ARM's original TrustZone security technology to maximize the security of the system.
That is to say, TrustZone divides the system into two parts: the secure world and the non-secure world. The non-secure core can only access the resources of the non-secure world, while the secure core can access all resources. Cryptocell is a hardware encryption/acceleration technology. For systems that pursue hardware performance, TrustZone Cryptocell technology can achieve outstanding system performance within a limited power budget. (The above is excerpted from EECHINA)
Now, with several chip companies launching Cortex-M23/33 processors, and the open source Trusted Firmware software supporting PSA functional API has been completed, Arm's PSA certification has been carried out smoothly. The first batch of PSA Level 1 certification has been completed in February this year, and Level 2 security certification is expected to be launched in the fourth quarter.
Rob said that in PSA Level 1 certification, the laboratory only needs one day to complete the questionnaire certification part, so if the chip company strictly follows the PSA framework requirements, then Level 1 certification will be very easy.
PSA Level 3 certification is expected to be completed in 2020. "I hope it can cover the trusted execution environment and security level on smartphones, and can protect applications such as fingerprint recognition and mobile payment." Rob said.
Arm is making great efforts to build a PSA certification platform
. Rob said that the starting point of PSA is to meet the most basic security needs. Although the Internet of Things is fragmented, different Internet of Things can have common security requirements, so it is hoped that PSA can cover 80% of Internet of Things applications. After meeting the basic security requirements, it will also communicate and cooperate with relevant certification organizations in some vertical industries, such as industrial or medical applications, to see how to let them refer to PSA certification.
Rob also emphasized that PSA is an open platform, and products with non-Arm processor architectures can also be used for PSA certification. Currently, PSA certification is moving towards standardization. In the future, there will be professional managers in the certification field, and there are plans to cooperate with a global standards organization (Global Platform) to make the entire PSA a standardized platform, operating in an association manner, in a more independent and open manner.
At present, the PSA certification project has been favored by many leading chip and IoT platform suppliers. These include many chip manufacturers, Cypress, Microchip, Nordic Semiconductor, Nuvoton Technology, NXP, STMicroelectronics and Silicon Labs, as well as OS such as ZAYA, Lierda, and Arm MBed.
For chips, most of the products that have passed PSA certification currently use the M23/M33 processor architecture, but Cypress PSoC64 uses the Cortex-M4F core and has also passed the certification. Rob said that the PSA certification standard mainly depends on whether the security function is met. The PSoC 64 security MCU device provides an isolated root of trust with real proof and configuration services. In addition, as more and more IoT devices adopt Cortex-A processors, PSA certification will also add this part of certification in the future.
Arm has set up a website specifically for PSA certification, https://www.psacertified.org/ . .org also means that the certification will be carried out in the form of an organization in the future, and the standards, processes, products, etc. of the certification can be queried from it.
Ecosystem jointly supports PSA certification.
As we all know, Arm has always been at the forefront of the industry in terms of ecosystem platform construction, and the same is true for PSA certification. PSA mainly provides security certification for IoT chips, underlying trust roots and trusted firmware, and provides a certified baseline security platform environment to meet the common security requirements of different vertical applications, so more and more companies need to participate. More
than a decade ago, Rob worked in Arm's mobile device business department, so he often came to China and was very familiar with the Chinese market, but this was his first time to recommend the PSA certification project in China. "There are many OEMs or solution providers in China who are willing to participate in PSA certification. We have also built a localized team to discuss security issues upstream and downstream of the industry chain and jointly promote the introduction and development of the PSA project."
In fact, no OEMs have passed the PSA certification yet, but Arm is ready to welcome these manufacturers to pass the first-level certification at any time. "In addition, there are some OEMs in China that use their own software and hardware platforms for commercial use, and we will also support such users." Rob added.
In order to better build an ecosystem, Arm has selected large certification laboratories in China, North America and Europe to cover different regions. At the same time, these laboratories have always been Arm's partners and have extensive experience in testing the trusted execution environment of mobile devices. Rob also looks forward to these partners continuing to maintain close cooperation in the field of the Internet of Things. 
From the arrangements of the PSA Security Architecture Technology Seminar, we can see that the participating manufacturers include independent testing organizations, chip manufacturers, OS manufacturers, terminal solution providers, consulting companies and cloud vendors, all of which come to the PSA certification platform.
Zhan Pengyi of Telecommunication Technology Laboratory said that the current Internet of Things has many problems such as OTA security risks, communication data security risks, authentication link security risks, and device security risks. In the IoT device attack experiment conducted by Telecommunication Technology Laboratory, the smart door lock was easily cracked, including one-time interception of passwords, OTA attacks, physical interference and other methods can be used to crack. For this reason, Zhan Pengyi said that the security testing of IoT devices requires comprehensive software and hardware testing, including hardware-level testing such as secure boot fault injection, key brute force cracking, side channel key recovery, and random number testing, as well as software-level testing such as firmware flashing, API fuzz testing, and rollback testing.
As an official domestic testing organization, TUV Rheinland Laboratory is also the only PSA authorized laboratory in China. Companies including Nordic, Nuvoton and Arm China have all completed PSA Level 1 certification with the help of TUV Rheinland Laboratory.
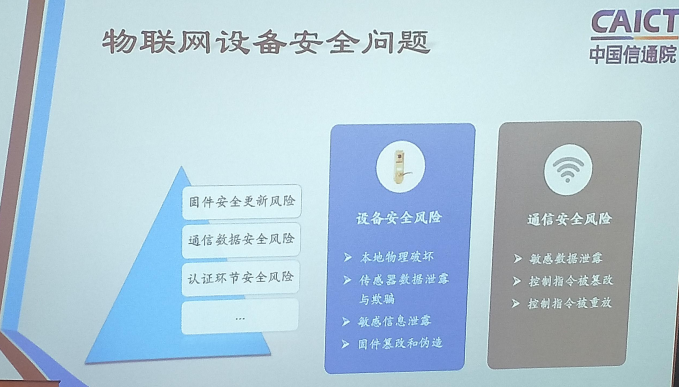
Security issues of IoT devices summarized by CAICT Labs
Zhang Kaifan of Brightsight said that Brightsight is the laboratory that cooperates most with Arm. Among the 26 products that have passed the PSA Level 1 certification, 20 are in cooperation with Brightsight, including NXP, Microchip, Lierda, ST, etc. Zhang Kaifan said: "The Internet of Things is a fragmented market. Terminal manufacturers do not have sufficient security capabilities and can only rely on other manufacturers' solutions. There is no evaluation standard. When terminal manufacturers choose solutions, they lack corresponding references and may only rely on price in the end. PSA certification can solve this problem well. So I also think that Arm is an important driving force for maintaining the security of the Internet of Things."
Zhang Kaifan explained that PSA certification is "stacked". For example, Lierda's OS uses STM32 chips for certification, but Lierda can reuse various certifications from ST. "It is relatively easier to pass verification using chips that have obtained PSA certification."
But Zhang Kaifan also emphasized that PSA is just a universal platform. It is difficult for terminal products to use PSA to replace the various security requirements of the Ministry of Industry and Information Technology, but basic requirements can be met through PSA.
Yu Qinghua, senior director of Unisoc, introduced Unisoc's comprehensive security strategy layout in the cloud, edge and terminal sides. Unisoc's dual-band WiFi 5 chip, based on the dual-core Arm Cortex-M33, realizes trusted operation partitions and secure peripherals, with secure boot and storage key protection and certification. Yu Qinghua said that this will be a smart and secure router, which will be protected throughout the life cycle and will not leak secrets at the end stage. At the same time, it will also be a smart router, including the entire home security control, and AI-related reasoning strategies can be executed. Christophe Mani of
STMicroelectronics introduced the security layout of ST's general-purpose microprocessors. He said that ST has always regarded security as one of the most basic elements of general-purpose MCUs, and also affirmed PSA certification. At the same time, he revealed that ST is currently undergoing PSA Level 2 certification, with a security level equivalent to EAL2, which will take about 25 days in total.
Zeng Xiang, deputy director of technology at Nuvoton Technology, said that in the past, security considerations for MCU manufacturers were to protect codes, but with the advent of the Internet of Things era, there are more means of cracking and intrusion, which has brought new requirements to security protection technology.

In the era of the Internet of Things, MCUs need to have more security features compared to traditional ones.
Zeng Xiang said that the threshold for MCU is very low at present. Companies such as Arm provide cores, which has enabled many manufacturers to enter this field. However, MCU is still a differentiated competitive market, and products will still have specific segmentation differentiation, which is mainly reflected in: 1. Architecture design, including the placement of IP, the trade-off between performance and power consumption, etc.; 2. Analog IP. In the past, MCU mainly sold Flash and RAM, but now most MCUs integrate more analog peripherals. At the same time, analog IP is not easy to buy, and requires its own core development team; 3. Low-power design; 4. Software and development tools; 5. Security, including secure storage, secure execution and secure connection.
Nuvoton Technology's M2351 has become the industry's first secure IoT microcontroller with Cortex-M23 core that has passed PSA Level 1 certification, and is expected to complete Level 2 certification in 2019. Because of its high security, this product can be used with a fingerprint recognition module on an identity authentication USB flash drive to achieve dual security mechanism FIDO certification. Or it can be used in secure communication modules, IoT door locks and other occasions that require security levels.
Zeng Xiang concluded that the Armv8-M architecture has upgraded the security of MCUs, and PSA has brought a security standard that can be followed for IoT MCUs. Despite this, the market for secure MCUs still needs continuous promotion and education so that the industry chain can pay enough attention to IoT security.
Previous article:MediaTek AI Partner Conference held to jointly promote the development of AIoT across the industry
Next article:Apple to open design and development accelerator in Pudong
- Popular Resources
- Popular amplifiers
- e-Network Community and NXP launch Smart Space Building Automation Challenge
- The Internet of Things helps electric vehicle charging facilities move into the future
- Nordic Semiconductor Launches nRF54L15, nRF54L10 and nRF54L05 Next Generation Wireless SoCs
- Face detection based on camera capture video in OPENCV - Mir NXP i.MX93 development board
- The UK tests drones equipped with nervous systems: no need to frequently land for inspection
- The power of ultra-wideband: reshaping the automotive, mobile and industrial IoT experience
- STMicroelectronics launches highly adaptable and easy-to-connect dual-radio IoT module for metering and asset tracking applications
- This year, the number of IoT connections in my country is expected to exceed 3 billion
- Infineon Technologies SECORA™ Pay Bio Enhances Convenience and Trust in Contactless Biometric Payments
- LED chemical incompatibility test to see which chemicals LEDs can be used with
- Application of ARM9 hardware coprocessor on WinCE embedded motherboard
- What are the key points for selecting rotor flowmeter?
- LM317 high power charger circuit
- A brief analysis of Embest's application and development of embedded medical devices
- Single-phase RC protection circuit
- stm32 PVD programmable voltage monitor
- Introduction and measurement of edge trigger and level trigger of 51 single chip microcomputer
- Improved design of Linux system software shell protection technology
- What to do if the ABB robot protection device stops
- Keysight Technologies Helps Samsung Electronics Successfully Validate FiRa® 2.0 Safe Distance Measurement Test Case
- Innovation is not limited to Meizhi, Welling will appear at the 2024 China Home Appliance Technology Conference
- Innovation is not limited to Meizhi, Welling will appear at the 2024 China Home Appliance Technology Conference
- Huawei's Strategic Department Director Gai Gang: The cumulative installed base of open source Euler operating system exceeds 10 million sets
- Download from the Internet--ARM Getting Started Notes
- Learn ARM development(22)
- Learn ARM development(21)
- Learn ARM development(20)
- Learn ARM development(19)
- Learn ARM development(14)
- Free gift of old punch card machine (for disassembly and research)
- Please help me look at this oscillator circuit
- About NCP1236 automatic recovery function test after removing short circuit and overload test
- Zigbee IoT module market: Differences between LTE standard Cat.1 and nbiot wireless communication modules
- ADS Installation Issues
- A Brief Discussion on FPGA Resource Evaluation
- MATLAB's UDP communication - How to send large batches of data packets via MATLAB's UDP
- [Blood Oximeter] Disassembly Part 4 Product Trial
- A P-MOS driving circuit
- DS18B20 Digital Temperature Sensor

 HA3-2544C-5
HA3-2544C-5
















 京公网安备 11010802033920号
京公网安备 11010802033920号