Ensuring functional safety and information security for Internet of Things (IoT) deployments is not just a matter of choosing the right protocols; it also relies on implementation processes as well as best practices and industry standards.
LoRaWAN is designed to be very secure - authentication and encryption are mandatory, however, if security keys are not kept secure and randomly distributed between devices, or if a once-used passphrase (random number) is reused, the network and devices can be compromised. Therefore, it is critical to look for a LoRaWAN CertifiedCM device to ensure that the device has been tested to security standards and works properly.
The LoRa Alliance has always kept security at the forefront of the development of the LoRaWAN specification and is highly transparent about the security features of the protocol (see Figure 1). The LoRaWAN specification was designed from the outset with security as a fundamental aspect, providing state-of-the-art security to meet the needs of highly scalable, low-power IoT networks. Unlike many other IoT technologies, the LoRaWAN specification already provides dedicated end-to-end encryption for application providers.
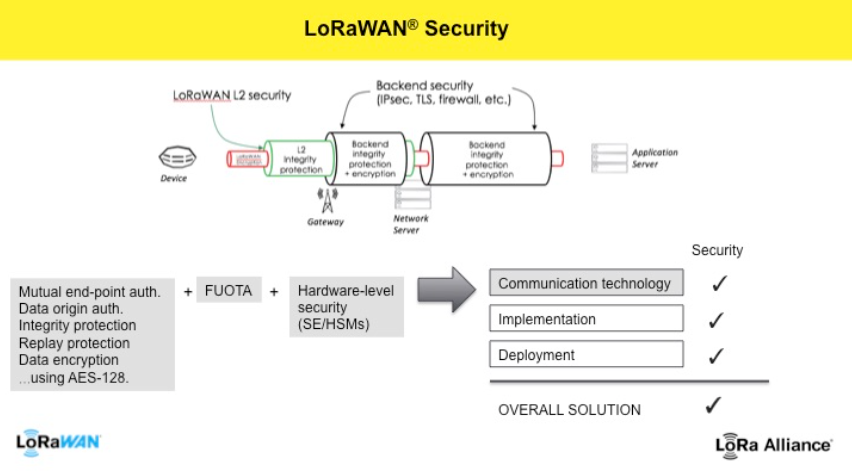
Figure 1: LoRaWAN security overview
The specification defines two encryption layers:
Uses a unique 128-bit key shared between the end device and the network server
Uses a unique 128-bit key (AppSKey) shared end-to-end at the application level
The AES algorithm is used to provide authentication and integrity of data packets to the network server and end-to-end encryption to the application server. By providing these two levels, a "multi-tenant" shared network can be achieved without the network operator having to see the user's payload data. The devices can be activated through personalization on the production line or during commissioning, or through over-the-air activation (OTAA) in the field. OTAA allows the key of the device session to be re-set when necessary.
LoRaWAN has all the basic building blocks required and used by any modern wireless communication technology and features AES-128. The inherent security of LoRaWAN provided in the specification needs to be accompanied by the secure implementation and secure deployment of these devices and/or networks to maintain the built-in security mechanisms of the protocol. It should be noted that this is true for all secure device implementations using any communication technology.
As mentioned above, LoRaWAN relies on symmetric cryptography, which requires keys to be shared in a secure and reliable manner. To further aid this process, LoRa Alliance members have developed:
The LoRaWAN backend interface isolates the storage of the root key in the joining server so that it becomes trusted regardless of the network
Secure element solutions that provide additional hardware physical protection to prevent tampering.
To ensure device and network security, as with any technology, best practices are always to use certified equipment and work with proven, trusted service providers. LoRaWAN is no different, and end users can have confidence in their deployment if they leverage resources that know how to properly implement a LoRaWAN solution.
Security is a moving target, malicious actors continue to emerge, and LoRaWAN is constantly evolving to address any new threats. While LoRaWAN is inherently secure, the LoRa Alliance is continually reviewing, designing, and implementing security enhancements and best practices to ensure LoRaWAN stays ahead of the changing security landscape.
Therefore, to help the market choose the right implementation, the LoRa Alliance will release a "Recommended Practices" document next month, which will provide device manufacturers with best practices to ensure the security of their devices. In addition, the Security Working Group reports to the LoRa Alliance Technical Committee responsible for the LoRaWAN specification and continuously reviews the security of technical specifications and documents. The Security Working Group is composed of security experts from LoRa Alliance members and works with academia to review documents and discuss security challenges.
Previous article:Sony Israel launches highly integrated NB2 chipset
Next article:Intel Thunderbolt technology celebrates its 10th anniversary, making connectivity easier
Recommended ReadingLatest update time:2024-11-16 12:55



- Popular Resources
- Popular amplifiers
- e-Network Community and NXP launch Smart Space Building Automation Challenge
- The Internet of Things helps electric vehicle charging facilities move into the future
- Nordic Semiconductor Launches nRF54L15, nRF54L10 and nRF54L05 Next Generation Wireless SoCs
- Face detection based on camera capture video in OPENCV - Mir NXP i.MX93 development board
- The UK tests drones equipped with nervous systems: no need to frequently land for inspection
- The power of ultra-wideband: reshaping the automotive, mobile and industrial IoT experience
- STMicroelectronics launches highly adaptable and easy-to-connect dual-radio IoT module for metering and asset tracking applications
- This year, the number of IoT connections in my country is expected to exceed 3 billion
- Infineon Technologies SECORA™ Pay Bio Enhances Convenience and Trust in Contactless Biometric Payments
- Innolux's intelligent steer-by-wire solution makes cars smarter and safer
- 8051 MCU - Parity Check
- How to efficiently balance the sensitivity of tactile sensing interfaces
- What should I do if the servo motor shakes? What causes the servo motor to shake quickly?
- 【Brushless Motor】Analysis of three-phase BLDC motor and sharing of two popular development boards
- Midea Industrial Technology's subsidiaries Clou Electronics and Hekang New Energy jointly appeared at the Munich Battery Energy Storage Exhibition and Solar Energy Exhibition
- Guoxin Sichen | Application of ferroelectric memory PB85RS2MC in power battery management, with a capacity of 2M
- Analysis of common faults of frequency converter
- In a head-on competition with Qualcomm, what kind of cockpit products has Intel come up with?
- Dalian Rongke's all-vanadium liquid flow battery energy storage equipment industrialization project has entered the sprint stage before production
- Allegro MicroSystems Introduces Advanced Magnetic and Inductive Position Sensing Solutions at Electronica 2024
- Car key in the left hand, liveness detection radar in the right hand, UWB is imperative for cars!
- After a decade of rapid development, domestic CIS has entered the market
- Aegis Dagger Battery + Thor EM-i Super Hybrid, Geely New Energy has thrown out two "king bombs"
- A brief discussion on functional safety - fault, error, and failure
- In the smart car 2.0 cycle, these core industry chains are facing major opportunities!
- The United States and Japan are developing new batteries. CATL faces challenges? How should China's new energy battery industry respond?
- Murata launches high-precision 6-axis inertial sensor for automobiles
- Ford patents pre-charge alarm to help save costs and respond to emergencies
- New real-time microcontroller system from Texas Instruments enables smarter processing in automotive and industrial applications
- A strange problem when compiling a KEIL project
- Micropython does not support GBK encoding
- The onboard microstrip antenna can completely replace the external IPEX antenna
- JTAG cannot recognize DSP processing
- What is a polarized relay?
- Reasonable use of NVM area
- Selection of chip beads and chip inductors
- How to put IAP at non-flash memory start address for Ateli AT32F403 microcontroller?
- 【Share】Choice of flyback chip
- Replace the foreign 2SK2837 field effect tube 500V, 24A model in AC-DC switching power supply!

 Application of LoRa on Raspberry Pi
Application of LoRa on Raspberry Pi Comparison of Lora, 433MHz, 4G and Wi-Fi communication technologies
Comparison of Lora, 433MHz, 4G and Wi-Fi communication technologies












 京公网安备 11010802033920号
京公网安备 11010802033920号